Critical Windows RDP Vulnerability: Immediate Action Required
Reliable and secure RDP (Remote Desktop Protocol) access is vital. A critical Windows RDP vulnerability, CVE-2025-53722, has emerged, allowing remote Denial of Service (DoS) attacks due to uncontrolled resource consumption. This flaw poses an immediate threat of severe operational disruption. It’s imperative to patch Windows RDP vulnerability across your systems without delay.

Understanding CVE-2025-53722: The DoS Threat
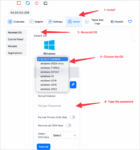
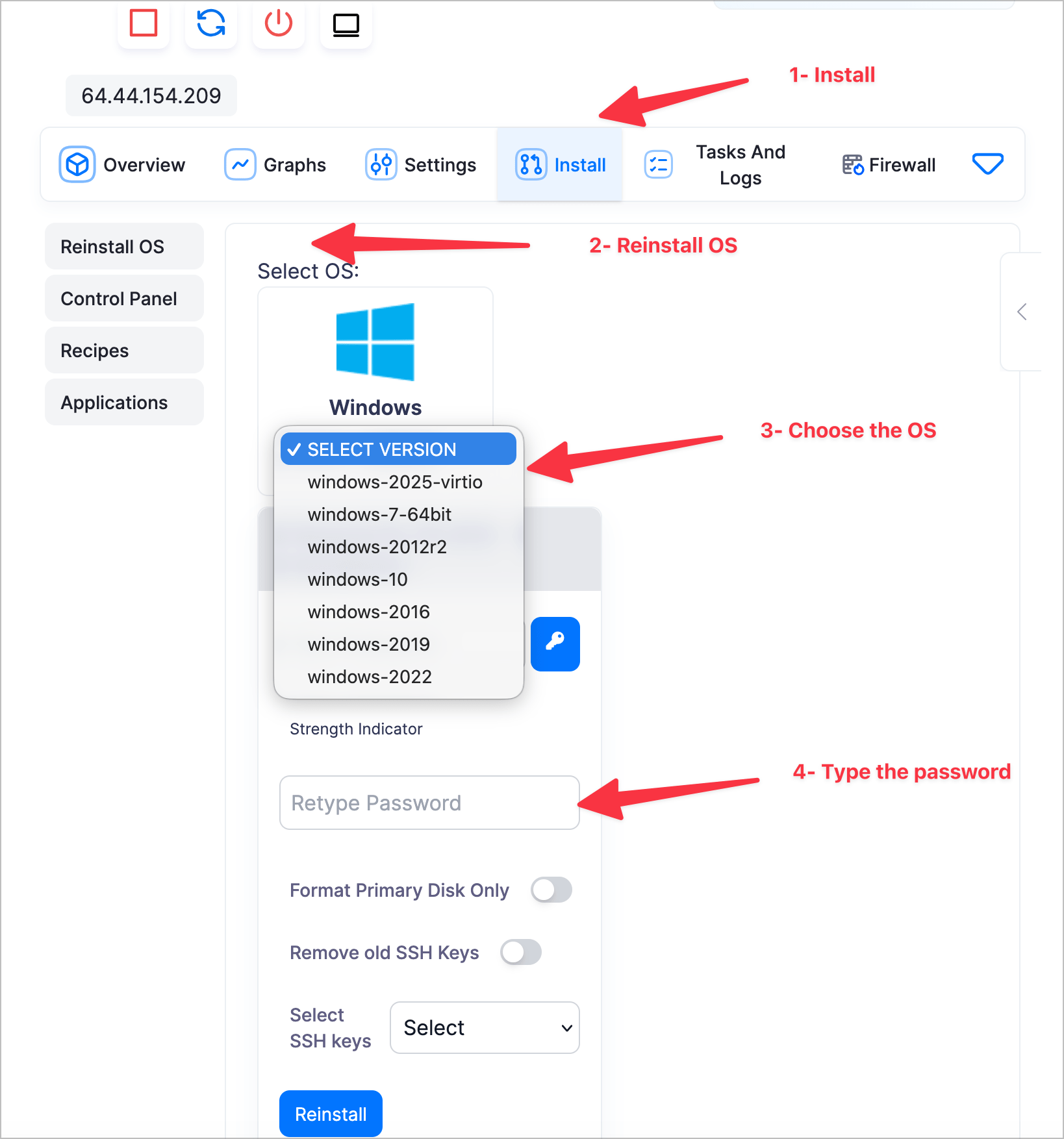
CVE-2025-53722 holds a CVSS 3.1 score of 7.5 (High severity). Its low complexity and network-based vector allow unauthenticated attackers to remotely overwhelm vulnerable RDP services, causing system inaccessibility. This impacts availability across numerous Windows versions, from Server 2008 R2 to Windows 11 (including 24H2) and Windows Server 2025. Microsoft released urgent security updates on August 12, 2025 (e.g., KB5063880 for Server 2022).
Benefits of a Secure RDP Server Environment
Beyond patching, a fundamentally secure RDP server environment offers crucial advantages:
- High-Performance: Enables fast, responsive remote sessions and efficient data transfer.
- Robust Privacy: Supports secure and confidential browsing, bypassing censorship.
- High Uptime: Ensures continuous availability of remote applications and services.
- Scalability: Allows flexible resource adjustments for evolving needs.
- Enhanced Security: Provides comprehensive protection against emerging threats.
| Feature | Standard RDP (Vulnerable/Generic) | High-Security RDP Solutions (Best Practices) |
|---|---|---|
| **Security Updates** | Often manual patching, potentially delayed, increasing vulnerability window. | Regular, timely patching and comprehensive security hardening. |
| **DoS Attack Resilience** | High vulnerability to DoS attacks like CVE-2025-53722 if unpatched. | Enhanced network infrastructure and robust security measures to resist DoS attacks. |
| **Connection Speed** | Varies widely; often limited by local network and generic infrastructure. | Dedicated high-speed connectivity for optimal performance and responsiveness. |
| **Uptime & Reliability** | Dependent on individual setup and local conditions; higher potential for downtime. | Engineered for maximum uptime with resilient infrastructure and redundancy. |
| **Privacy** | Basic; dependent on user’s own security practices and network environment. | Enhanced privacy features and secure connection protocols. |
| **Flexibility for Payments** | Typically limited to widely accepted conventional payment methods. | May offer diverse payment options, including secure digital currencies for enhanced privacy. |
| **Scalability** | Often requires significant manual configuration or service interruption for upgrades. | Designed for easy, on-demand resource upgrades with minimal to no service interruption. |
Immediate Action to Secure Your RDP
To protect against this Windows RDP vulnerability and similar threats:
- Prioritize Official Patches: Immediately apply Microsoft’s security updates for CVE-2025-53722.
- Harden Network Access: Restrict RDP access via firewalls or VPNs.
- Implement Vigilant Monitoring: Watch for unusual RDP traffic patterns.
- Consider Robust RDP Providers: Leverage service providers handling infrastructure and security updates.
- Regularly Review Security Posture: Maintain strong passwords, MFA, and disable unused RDP.