
Urgent: Patch Windows RDP Vulnerability (CVE-2025-53722) Now!
Critical Windows RDP Vulnerability: Immediate Action Required Reliable and secure RDP (Remote Desktop Protocol) access is vital. A critical Windows

Critical Windows RDP Vulnerability: Immediate Action Required Reliable and secure RDP (Remote Desktop Protocol) access is vital. A critical Windows
This tutorial will guide you through installing the full Ubuntu Desktop environment (GNOME) on an Ubuntu Server VPS and setting

Virtualization has transformed the way we use computers, allowing us to run multiple operating systems on a single physical machine.

Recent Windows Server updates have triggered Kerberos authentication failures, severely impacting RDP security and disrupting vital secure RDP connection to

The latest WinRAR vulnerability is a serious wake-up call for anyone managing files on a Windows VPS or RDP server.
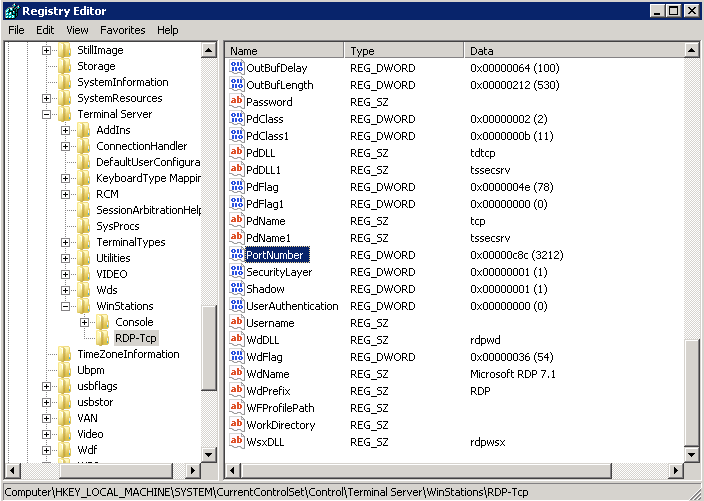
Remote Desktop Protocol (RDP) allows remote administration of Windows systems over a network connection. It enables users to access GUI

Is your Remote Desktop connection truly secure? Cybercriminals are constantly searching for vulnerabilities, and Microsoft’s February 2025 Patch Tuesday has
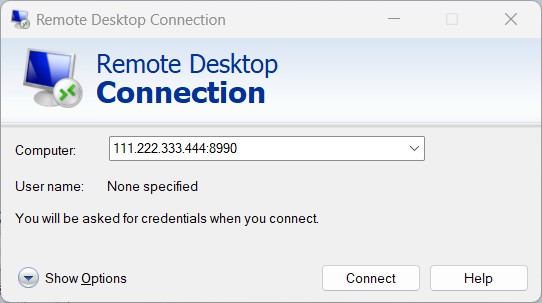
Introduction Do you need to access your Windows system remotely but can’t figure out how to enable RDP? You’re not

Aminserve is excited to welcome 2025 with a special offer for our valued users. We’re giving away 500 USA RDP

A new critical vulnerability, CVE-2024-49115, has been discovered in Windows Remote Desktop Services, putting countless systems at risk. If exploited,
Fast solution: Download and move this file to your RDP. Run it inside your RDP to create a new remote

In the ever-evolving landscape of remote work and IT management, reliable remote desktop applications have become essential. Whether you’re troubleshooting